I finally decided to set up a real router in front of my router. The main use cases, I wanted to cover were the following:
* nice local domain names: Since I run a FritzBox (which is a pretty common plastic router in Germany), all local host names (sometimes!) get suffixed by .fritz.box. This domain cannot be configured to .something.awesome and the whole setup is quite in-transparent, that I could not figure out, in which cases, the suffix is mandatory when resolving host names.
* play around with [snort](https://www.snort.org/).
* bandwidth monitoring: to replace the current workflow of randomly killing machines, when the internet connection is slow and one needs bandwidth to do something important™.
In this blog post I will cover nothing of this. Instead, I'll explain, how I set up a RaspberryPi to enable me to do all the above in the future.
## Overview
Here is the obligatory visualization:
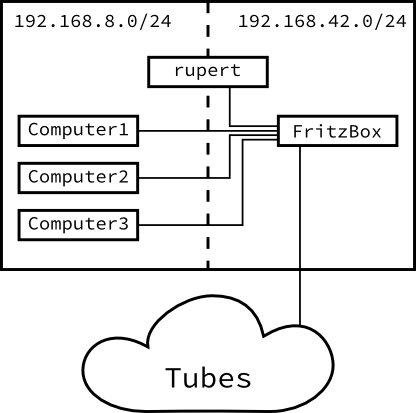
So there will be two network, one with the FritzBox and the Pi (called
rupert) and the other with the Pi and all the other computers. They are not divided in a physical level (shown as the "wires" connecting the boxes) but merely by software.
## Install Raspbian
Install the latest version of Raspbian to your RaspberryPi. You know the drill. I used a [http://amzn.to/2p7Cwya](RasberryPi 2) as hardware but don't know yet, if it has too much or not enough resources. I figured, that it will probably be more powerful than the FritzBox ¯\_(?)_/¯.
## Network Layout
I decided to create two networks: 192.168.8.* and 192.168.42.* ((or, to be more precise 192.168.8.0/24 and 192.168.42.0/24)). I'll call the first of those networks N8 and the second one N24 in this blog post. The Raspberry –
let's call him rupert from now – will be responsible for routing between the two networks. All local computers should be part of N8. N42 should only contain rupert and the FritzBox.
As a nice bonus, the USB port present on my FritzBox has enough power for rupert, so there are only two cables connecting the two: USB for power and the ethernet cable of course.
## Configure FritzBox
The FritzBox can completely be configured by skillfully clicking around in the web interface (make sure, to enable the advanced view though). So we don't require to change the firmware, which allegedly would void the warranty.
* Change the IP address of the FritzBox to 192.168.42.1
* Disable the DHCP server, rupert will do this
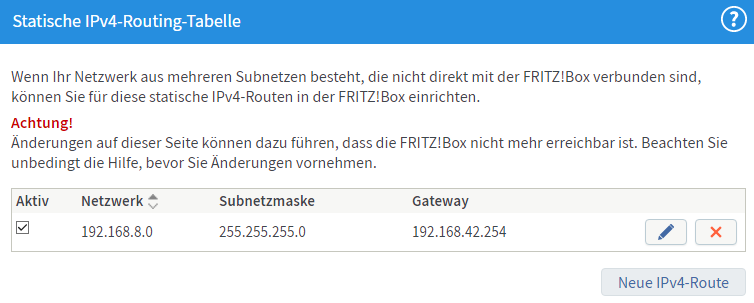
* Create a static route on the FritzBox to the network 192.168.8.0/24 with a Gatway of 192.168.42.254 (which will be rupert's IP in N42), this is necessary because of devices wirelessly connecting to the FritzBox
## Configure RaspberryPi
We will use iptables for routing and dnsmasq as a DHCP server and DNS proxy. So make sure, these two packages are installed. Since the Pi only has one ethernet interface, we need to set up a so called sub interface on eth0 for N8. We also need to bridge between the two networks.
auto lo
iface lo inet loopback
# primary network interface
auto eth0
iface eth0 inet static
address 192.168.42.254
netmask 255.255.255.0
network 192.168.42.0
broadcast 192.168.42.255
gateway 192.168.42.1
# sub interface
auto eth0:1
iface eth0:1 inet static
address 192.168.8.1
netmask 255.255.255.0
# DNS servers
dns-nameservers 192.168.8.1 192.168.42.1 8.8.8.8
# bridging
iface br0 inet dhcp
bridge_ports eth0 eth0:1
pre-up ifconfig eth0 0.0.0.0 up
pre-up ifconfig eth0:1 0.0.0.0 up
pre-up brctl addbr br0
pre-up brctl addif br0 eth0
post-down ifconfig eth0:1 0.0.0.0 down
post-down ifconfig eth0 0.0.0.0 down
post-down brctl delif br0 eth0
post-down brctl delbr br0
/etc/sysctl.conf:
net.ipv4.ip_forward=1
dnsmasq, I added or uncommented the following lines of /etc/dnsmasq.conf:
interface=eth0
dhcp-range=192.168.8.20,192.168.8.200,12h
dhcp-option=option:router,192.168.8.1
dhcp-option=option:dns-server,192.168.8.1
# use FritzBox as NTP server
dhcp-option=option:ntp-server,192.168.42.1
iptables -F
iptables -X
iptables -A INPUT -i lo -j ACCEPT
iptables -A OUTPUT -o lo -j ACCEPT
iptables -A INPUT -i eth0:1 -j ACCEPT
iptables -A OUTPUT -o eth0:1 -j ACCEPT
iptables -A POSTROUTING -t nat -o eth0 -j MASQUERADE
iptables -A FORWARD -i eth0:1 -j ACCEPT
/etc/network/if-up.d/router.sh to run it, when your interface goes up (don't forget to +x).
Update on 2017-04-17: the IP of rupert itself resolved to 127.0.1.1 not only on the Raspberry itself but in the whole network. Changing the corresponding line in /etc/hosts to
192.168.8.1 rupert
/etc/dnsmasq.conf: filterwin2k, cache-size=500. Both are probably only performance optimization
* I disabled all UPnP feature on the FritzBox. This may be less confusing for some other programs and may be a good idea anyways.
Also, this setup has the obvious problem, that the two networks are not separated physically: someone, who knows, what he or she is doing can simply take a static IP in N42 and bypass rupert. On the upside of things, you can still google stuff while settings this up simply by giving your machine a static IP in N42.
Since you will not be able to connect to the FritzBox web interface from N8 anymore, I suggest an SSH tunnel through rupert for this.
One Reply to “Snort on Raspberry Pi behind FritzBox!”