This post will explain, how to identify a function responsible for string deobfuscation in a native-PE malware sample. We will use a KpotStealer sample as a concrete example. KpotStealer (aka Khalesi or just Kpot) is a commodity malware family probably circulated in the shadowy parts of the internet since 2018. It got its name from a string publicly present on the Admin-Panel.
After we found the function we will understand the data structure it uses and emulate the decryption of a string with CyberChef and Binary Refinery. An interesting detail here is that Ghidra currently does not guess the function signature correctly.
Finally, we will develop a Java script (hehe) for Ghidra to automatically deobfuscate all strings given the corresponding obfuscation function.
Show me what you got!
There are two central problems that I faced with Slack:
1. Slack feels like I am developing in Eclipse, in a Windows VM, on an old Linux laptop. Where does all the bloat come from? It can't even have more than one channel open at a time!
2. In some cases, Slack can [force you to log out][SlackTimeout] after 12 hours, say. I understand why you would check that box as an IT admin, but I will show you that Slack is currently not enforcing this policy, and so I'd prefer to not be subject to it. 😼
## Good Slack Clients
The first problem is rather easy to solve, you simply use an alternative client. There are three options I am aware of:
- Using [WeeChat][] with the [WeeSlack][] plugin. I also recommend the [WeeEdit][] plugin to post multi line messages, especially for those code blocks. Finally, I use [WeeAutosort][] because the list of slack channels in WeeChat is a little confusing otherwise. This client is certainly your best option if your top priority is to go open source, to get it for free, or to use it on the command line. And it is a really good way to use Slack, too. I like it very much.
- You can use [Pidgin][] with the [slack-libpurple][SlackLibPurple] plugin. Unfortunately, I have to say that this works rather poorly and I mention it here only to be complete. I thoroughly recommend WeeChat if you are absolutely not willing to use a commercial and closed source program; it is better to use WeeChat with [WeeSlack][] in a terminal for Slack than to use the Pidgin plugin.
- If you are willing to pay $20 for your happiness, you should buy [Ripcord][] (Win/Linux/Mac supported). Even though it is in Alpha, it is the best Slack (and Discord!) client I have used. It supports Slack features in a more natural way because it is built specifically to do so, where in WeeChat some things may be awkward (inline images, navigating threads, etc). It is fast, has a low memory footprint, feels snappy, and gives you tabs for channels, DM's and threads. It is my weapon of choice.
[AndroidEmulator]: https://developer.android.com/studio/run/emulator
[AndroidEmulatorNetworking]: https://developer.android.com/studio/run/emulator-networking
[Ripcord]: https://cancel.fm/ripcord/
[MITMProxy]: https://mitmproxy.org/
[Pidgin]: https://pidgin.im/
[HAR]: https://en.wikipedia.org/wiki/HAR_(file_format)
[SlackLibPurple]: https://github.com/dylex/slack-libpurple
[WeeChat]: https://weechat.org/
[WeeSlack]: https://github.com/wee-slack/wee-slack
[WeeSlackSecure]: https://github.com/wee-slack/wee-slack#4-add-your-slack-api-keys
[SlackTimeout]: https://slack.com/intl/en-de/help/articles/115005223763-Manage-session-duration-?eu_nc=1
[SlackAPI]: https://api.slack.com/web
[SlackOverflow]: https://stackoverflow.com/questions/11012976/how-do-i-get-the-apk-of-an-installed-app-without-root-access
[NougatChanges]: https://android-developers.googleblog.com/2016/07/changes-to-trusted-certificate.html
[WeeEdit]: https://raw.githubusercontent.com/keith/edit-weechat/master/edit.py
[WeeAutosort]: https://raw.githubusercontent.com/de-vri-es/weechat-autosort/master/autosort.py
[WeeOTR]: https://raw.githubusercontent.com/mmb/weechat-otr/master/weechat_otr.py
## Loot Slack Tokens from Mobile
Now if you want to come along and get around periodic logouts in Slack with me, we'll have a bit of work to do.
This post describes the memory layout as well as the method used by the Sodinokibi (or REvil) ransomware to protect its strings. It will then list a few Java snippets to interact with the Ghidra scripting API and finally explain a working script to deobfuscate all strings within a REvil sample. If you don't care about the explaination, you can find the most recent version of the script you can simply import into Ghidra on github.
I want it all.
Since the temperature of scripting in Ghidra is so high at the current point in time, I want to tell you that scripting it in Java is so much better than scripting it in Python. After that I'll randomly motivate why one wants to get the "original bytes" from a sample and how to do it.
Show me what you got!
Found another rabbit hole! While reading my daily digest of tubes [an article about the Mozi bot](https://blog.netlab.360.com/mozi-another-botnet-using-dht/) sparked my interest. Peer-to-peer (P2P) botnets are always cool and this one has some worm-like capabilities and seems to hide its traffic within bittorrent communications. Naturally I wanted to take a look at the sample.
But you will not believe, what happened next!
I have spent some time reverse engineering Delphi binaries with IDA & HexRays at work, but IDA tends to make a few mistakes and I wrote a few scripts to fix them. Then [Ghidra](https://ghidra-sre.org/) came along and I was very curious to know how it would fare against some of the Delphi malware that I know and ~~loathe~~ love. I'd say it does about as bad as IDA, and so I went on a journey to rewrite my scripts from work as Ghidra scripts. TL/DR; [The scripts are on GitHub](https://github.com/huettenhain/dhrake/). But would you like to know **more**?
While understanding existing code during software development or reverse engineering, it is quite useful to be able to quickly see other instances of the same variable or function in the current code view. To enable this feature in Ghidra, I suggest you perform the following two configuration changes:
Under "Edit" → "Tool Options..."
1. select "Listing Fields" → "Cursor Text Highlight" in the tree view on the left and change "Mouse Button To Activate" to "LEFT"
2. select "Key Bindings" in the tree view on the left and assign a key you can easily press to "Highlight Defined Use" ("SPACE" for example)
Happy understanding!
Update (2019-11-22): Actually "Highlight Defined Use" refered to in item 2. of the above list is not the same as the highlighted parts from item 1 :sadkeanu:.
This post is written for aspiring reverse engineers and will talk about a technique called _API hashing_. The technique is used by malware authors to hinder reverse engineering. We will first discuss the reasons a malware author may even consider using API hashing. Then we will cover the necessary technical details around resolving dynamic imports at load-time and at runtime and finally, will described API hashing and show a Python script that emulates the hashing method used in Sodinokibi/REvil ransomware.
Read on
It's 2019. People get paid for playing Starcraft. As someone who does not, I'm trying to get into watching the games by following the currently held World Championship Series 2019 in Starcraft 2. Even after 20 years I think Starcraft has lost nothing of its fascination. I'm enjoying watching the game now as much as I enjoyed playing it when it was first released.
Read on
Earlier this year, I was thrilled to hear that my submission for a talk at this year's [FrOSCon](https://www.froscon.de/) (Free and Open Source Software Conference) was accepted. [The talk](https://programm.froscon.de/2019/events/2350.html) is about Ghidra, the reverse engineering tool which was recently release into open source by the NSA. Since I expected a very heterogeneous audience with people from all kinds of industries with all kinds of backgrounds, I decided to give a long introduction with a lot of motivation for reverse engineering and only use the last quarter or so of the talk to actually show Ghidra's capabilities.
You can find the [slides here](https://blag.nullteilerfrei.de/wp-content/uploads/2019/08/FrOSConTalk2019-Ghidra.pdf), the source [of the slides on github](https://github.com/larsborn/FrOSCon2019-Ghidra-Talk) and a recording at [media.ccc](https://media.ccc.de/v/froscon2019-2350-ghidra_-_an_open_source_reverse_engineering_tool). Based on feedback after and during the talk, I added a bullet point under Motivation: a lot of people at FrOSCon seemed to be in the position where a wild binary blob appeared and they had to deal with it. Some because they found an old service running with source code not available (or readable) anymore and some because they want to re-implement a protocol that is not documented.
A while back [I blawgd about how to get the MSDN library for offline use](https://blag.nullteilerfrei.de/2017/12/21/get-the-msdn-library-for-offline-use/). However, the Help Viewer has its problems. I won't list all of its problems, but it was certainly a bad candidate to integrate Win32 API documentation support to Ghidra. There is [a pretty neat project by Laurence Jackson](http://laurencejackson.com/win32/), but I think I just found something a little better even: Microsoft provides [a download of the MSDN Library for Visual Studio 2008 SP1, stand-alone, offline, as an ISO](https://www.microsoft.com/en-us/download/details.aspx?displaylang=en&id=20955) - smell this, Help Viewer:
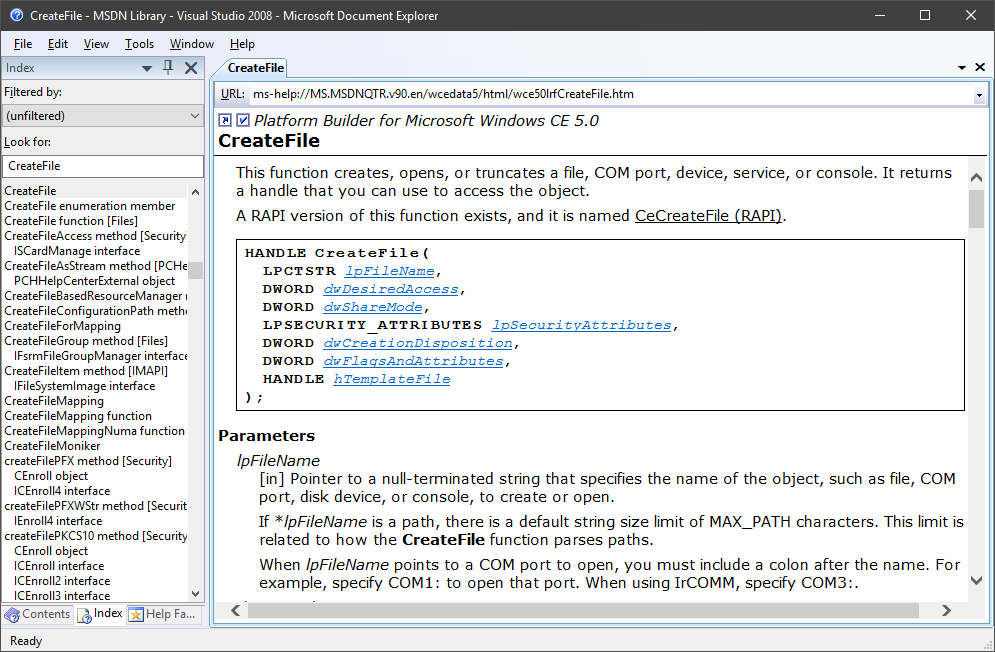 So this is nice, but the main point of this exercise was to integrate this into Ghidra. If that's something you care about, read on.
So this is nice, but the main point of this exercise was to integrate this into Ghidra. If that's something you care about, read on.
 So this is nice, but the main point of this exercise was to integrate this into Ghidra. If that's something you care about, read on.
So this is nice, but the main point of this exercise was to integrate this into Ghidra. If that's something you care about, read on.
After a system crash, Ghidra greeted me with the message
Unsupported file system schema: idata
Say you want to write a C program, but you want to avoid including plain strings within the binary. This is something often done by malware authors, for example, to avoid easy extraction of so called indicators of compromise. I can also imagine a legitimate business that uses string obfuscation to make reverse engineering of their software harder to protect their intellectual property.
This is often called string obfuscation.
I want to use this knowledge to make the world a better place!