I recently noticed that
RdrCEF.exe was clocking close to all of my CPU cycles. This is a cloud service built into Adobe Reader DC, which [constantly sends all kinds of information to Amazon](https://forums.adobe.com/thread/1811609). Leaving all the privacy concerns aside, my computer became inoperable by opening a PDF document. Okay, here's how you fix this.
* Download the [Adobe Wizard](http://www.adobe.com/devnet-docs/acrobatetk/tools/Wizard/), most likely [the version for Adobe DC](http://www.adobe.com/devnet-docs/acrobatetk/tools/Wizard/WizardDC/basics.html).
* Put on your robe and your wizard hat.
* Get yourself your preferred [Adobe DC Installer](ftp://ftp.adobe.com/pub/adobe/reader/win/AcrobatDC/1500720033/), and **make sure it's the MSI version**.
* Use the Wizard to open the MSI and do this:
[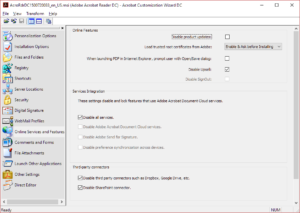](/wp-content/uploads/2016/09/wizard.png)
* Save the MSI and install your new AdobeDC.
Of course, feel free to customize your AdobeDC installer in any other way.